Certificate authorities (CA) are trusted parties that provide parties to
secure communication with digital certificates. Secure Socket Layer protocol (SSL) requires the use
of certificate authorities who ensure authenticity of the communicating parties
and provide them with encryption keys for secure communication.
Currently there are only a few CAs and the most commonly used is Verisign.
There are three strategies for procuring services of CAs:
- Organisations
that require the services of CAs usually outsource their requirements from
companies like Verisign or companies (CAs) that are certified by any one
of the trusted certificate authority. Under
these circumstances Verisign is referred to as an external CA.
Using an external CA is the cheapest and the most straight forward
option with no need for extensive training or start up fees. One
drawback of using external CAs is that it reduces organisational control
over confidentiality of information. In
essence this amounts to getting an external company to install the organisation's
SSL secured Web server.
- Some
of the organisations that require internal control and greater confidentiality
or have certain constraints in their security policy opt for developing
an internal agency called a private CA to issue organisational digital certificates.
This provides absolute control over the organisational security of
information. This is expensive to set up and one that
requires specialised hardware, and more importantly trusted personnel that
need to be trained to run the CA.
- Another
strategy is to go for a combination of external and internal CA. For example Verisign offers services whereby
organisations can build internal CAs while taking advantage of considerably
lower investment. In other words,
organisation outsourcers the right to issue, suspend, manage and renew digital
certificates that are labelled with the organisation's brand.
The function of validating and approving applications for certificates
is also retained by the organisation. This
strategy is particularly useful when the corporate comprises of numerous
departments that require CA's services.
Essentially a private CA is formed for the Intranet to approve and
issue digital certificates to internal Web servers. The corporate is approved and trusted by
the external CA and therefore issuing certificate could also be extended
to Web servers that customers and business partners may use.
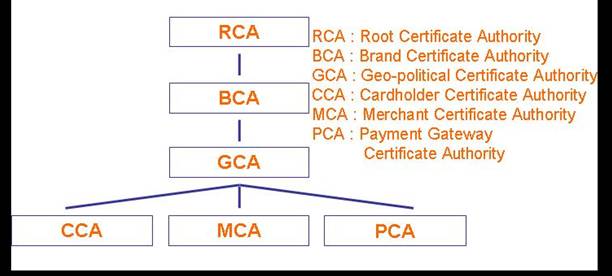
CAs have hierarchical infrastructure:
- At
the top of the hierarchy we have the root CA. Usually within a business sector, for
example banking, manufacturing, or publishing, a certificate authority if
formed to act as a root CA. These
collaborations are usually international.
Root CA's function is to certify the certificates that are used by
the organisations that are involved in the collaboration. One example of such CA is 'Identrus', which is formed by a number
of American, German, British, and Japanese banks. Identrus acts as the root CA to verify
certificates that are used by the banks involved. Use of root CAs also help businesses
benefit from standard operating rules, practices and procedures and put in
place contractual obligations. All
business transactions leave clear trail, which help resolve disputes. The question off course remains as to
the body that is to regulate or certify the activities of root CAs. At the present time there is no clear
indication as to who may fulfil this role although U.S. Post office is
envisaged to play a part. Root CA
is placed at the highest level of hierarchy to suggest that all CAs have
to be approved by another CA at higher level of hierarchy. Lack of cohesiveness exists as to the hierarchy
of the certificate authorities and it is generally believed that a number
of root authorities may eventually emerge.
- Strong
brands are also emerging as CAs. American
Express, MasterCard, and Visa are among the brands that are envisaged to
play a considerable role, in particular to promote electronic trading and
ease of online payment. The idea is that consumers obtain certificates
from their credit card companies. In
turn digital certificates are attached to credit card payment transactions.
Visa and MasterCard have been the driving force for the development
of Secure Electronic Transaction protocol (SET).
Use of certificate ensures authenticity of the consumer and SET protocol
ensures that the only information that is divulged to the merchant is the
order information and not the consumer's payment details.
- In
order to promote electronic commerce on global scale, there is a need for
CAs that can operate internationally.
Geo-political CAs issue certificates to certify companies that
intend to act as commercial CAs worldwide.
This service is basically a stamp of approval and acts as a
motivator of electronic commerce.
- At
the bottom of the hierarchy are the entities that actually use the
certificates. Consumers, merchants
and payment service providers are examples of entities that engage in
electronic trading and in particular need to ensure authenticity of one
another.
Some of the short comings of CAs are:
- Compatibility:
Digital certificates are not necessarily interchangeable. Most certificates that are issued by
credit card companies are geared towards purchasing goods on the Internet
from online merchants. The can not
necessarily be used to obtain services for example from government offices
or they can not be used for signing sensitive legal documents such as
legal deeds and agreements.
- International
recognition: Globalisation is at the present time a vision. Not all nations have legislation in
place to accept digital certificates as legally binding. Furthermore, due to the lack of
international standards, there is no internationally accepted authority to
overlook the activities of CAs in different countries. Certificates are only as credible as the
reputation of issuer. It therefore
becomes one of understanding between two trading partners as to the trustworthiness
of CAs.
Consumer generates his key pair and sends the public key to the CA along
with some required credentials. CA
checks the identity of the applicant and ensures that the request has actually
come from the applicant and that public key of the applicant has not been
modified in transit either accidentally or maliciously. The certificate that is issued certifies the
binding between the applicant and his public key. It also includes the hierarchy of
certificates that verify the public key of the CA or it includes the CA's
public key. It is the legitimacy of his
public key that the consumer demonstrates by presenting the hierarchy of
certificates along with his public key to the merchant.
|
Which
certificate authorities does your IE browser trust? Can you remove one from the list of trusted
ones? What are the implications If you
do remove them? |
|
|
|
Cross certification is used frequently
and is important as an enabler of commercial transactions. What is cross certification? How does it help? |
|
|
|
As
students, do you see a part for the university to potentially play as CA to
issue you with digital certificates? Discuss. |
|
|