Open System
Interconnection (OSI) reference model is an attempt to model the digital communication
between two applications. Another words
this is an attempt to conceptualise and encapsulate the required functionalities
for the transfer of information from an application on a sending machine to
the application on the receiving machine in seven distinct layers, each of
which is a collection of particular functionalities and performs a value-added
service. If we think of all functionalities
as a collection of routines (each of which does a particular job), then services
of a number of these routines are called upon when an application initiates
a process that includes communication
with another machine. Most of these
routines are called by other routines and most of these calls are hidden from
the application altogether. So we can batch together these routines in
an hierarchical layering system in such a way that services of a routine at
a layer is called upon by a routine placed in the layer above. This batching process is called layering.
The term open is reference to interoperability.
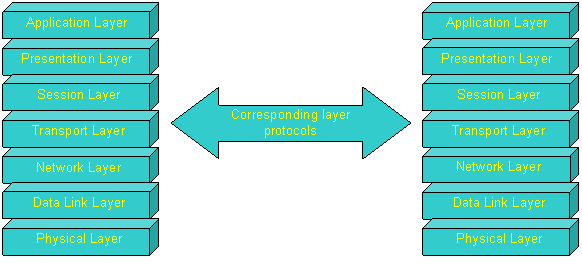
OSI reference
model in effect describes the architecture in the form of seven layers at
each end of communication. Each layer
has a corresponding layer on the other side and effectively the two corresponding
layers understand each other through common protocols between them.
You should also note that the OSI model does not only refer to TCP/IP
networks or Ethernet networks but to all types of network.
On the side
of the sender information travels from the application layer to the physical
layer. Physical layer is a model of
the physical connection between the two computers such as
ISDN and/or coaxial cable. Information
is then passed on up the hierarchy of the seven layers on the receiving end
from the physical layer to the application layer. It's a bit like posting a letter when letter
is place in an envelope, it is stamped and addressed except that in this case
this happens a number of times and the envelope gets thicker and thicker. The job of a layer is to receive the envelope
from a higher level layer and do the required processing to the envelope,
place the product in a bigger envelope, stamp and address it to your corresponding
layer on the other side and pass it on to the lower layer. On the side of the receiver the corresponding
layer's job is to receive the envelope from the lower layer (remember It is
addressed to this layer), open it and do the required processing (which is
to realise the envelope) and pass the original envelope to the layer above.
In a little
more technical terms, a layer receives information from the layer above, processes
the information, adds its header to the information and passes it to
the layer below. On the other side the corresponding layer receives
the information from the layer below, strips the header from the original
piece, opens the header and performs the required processing according to
the content of the header and passes on the original information to the layer
above.
For example
transmission layer receives information from the session layer, divides the
information into manageable segments called packets and (depending on what
protocol is being used at this layer) adds to each packet particulars such
as identity of the connection, information that would help check the integrity
of the packet, sequence number of the packet in the information (packets may
not arrive in the right sequence), ....and passes the slightly bulkier packet
to the network layer. On the other
side transmission layer receives the packet from the network layer, reads
the information added by the sender's transmission layer, depending on the
protocol at hand (the same protocol used by the sender) does some processing
such as reassembling the information using the sequence numbers, making sure
of the integrity of the packet using the integrity check information,...and
send the recovered information to the session layer.
Application
layer's job is to interface with the user and 4provide the required services.
Examples of these services could be E-mail, file transfer, newsgroup,
file services, ....
Presentation
layer is concerned with the syntax and semantics of data to be transferred. It is about how data is to be presented. Examples of standard for data presentation could
be ANSI or HTML. Also there are those
standards that specify basic data characteristics such as the bit-size of
integers or whether or not the standard is to write from left to right. There are also those functions that may be
quite common from a user to user. Instead of solving the function for each
user the idea is to find a general solution to the problem. A good example is the Domain Name Service where
the IP addresses to those domain names that are frequently requested to be
resolved may be cached. Examples of
protocols in this layer are POP/SMTP, Telnet, Usenet, DNS,
Http, Ftp, ...
Session
layer regulates the session. It manages
the process of who's turn it is to send data.
In some networks only one host can use the channel at the time and
conversation alternates between the hosts.
This is done through use of data token where a host can send data only
when it possess the token. Examples
of protocols in this layer are POP/25, 80, 53, RPC Portmapper,..
Transport
layer is about the control of flow of data from the sender to the receiver
and ensuring that data has got there. It
divides the data into manageable chunks
and adds additional information to the packets to identify the packet in the
sequence, and what the characteristics of packet is. These characteristics are then checked against
the packet at the destination and acknowledgments are forwarded to the sender.
As such transmission is highly reliable.
Nevertheless there are protocols in this layer that do not do rigorous
checking. Transport layer could be considered as an interface
in the OSI stack between application oriented layers and technology layers.
It is at the boundary between the two communicating hosts and the communication
links (the work of routers, bridges etc).
It is the last end-to-end layer in the stack.
Examples of protocols are TCP, UDP, SSL...
Network
layer is responsible for routing the data from the sender to the receiver. It does no error checking and as such the protocols
at this layer are referred to as unreliable. This routing could be according to static information
that is predetermined for the network and programmed into it. Routing information could also be determined
through handshake process at the start of the communication. It could also be highly dynamic when routes
are determined according to the real-time traffic state of the network. Examples of protocols at this layer are IPv6,
IPv4.
Data link
layer specifies the access strategy for sharing the physical medium. The layer on the sender breaks the data up into
frames which are sent sequentially. It
also receives acknowledgement from the receiver. Regulating the traffic also gets down in this
layer although some of the other upper layers do this too. The idea is not to overwhelm a relatively slower
receiver. Examples of protocols are
Ethernet, SLIP, PPP....
Physical
layer defines the physical characteristics of the network. Here we are concerned with for example what
kind of wire and connection we use and basically the electronic signals. Examples are ISDN, ADSL, Coaxial cable, ... Most of the functionality here is taken care
of by the NIC card in your PC through interfacing with the routers.
Often the
7 layer model is simplified to a 4 layer model in case of internet applications.
Application layer, Transmission layer or sometimes referred to
as TCP layer, Network layer or sometimes referred to as IP layer, and physical
layer. References to layers as TCP
and IP layers are not strictly speaking altogether correct as TCP and IP are
just protocols at these two layers and by no means the only ones used for
communication on the Internet. However
these are the most important two and hence the takeover by names. An example would be sending an Email for which
an application protocol for Email is used. This protocol basically defines a set of commands
for specifying who the sender is, who the receiver is and what the content
of the Email is. What this protocol
does not concern itself with is how the communication is taken care of.
This is a typical application layer protocol all of which use the services
of the TCP and IP for the communication bit of the job.
So this mail is passed on to the TCP layer.
If this message is larger than allowed for a packet, TCP breaks in
into a number of manageable ones and passes them to the IP layer.
TCP also makes sure that each and every one of those packets do safely
arrive on the other side. IP on the
other hand does not concern itself with ensuring that packets do actually
arrive on the other side. Its job is
to route the packets from the sender to the receiver using the address supplied
by the application layer. Transmission
of electric pulses are taken care of at the physical layer and protocols that
mange the specific physical medium such as Ethernet or point-to-point come
into action at this layer.