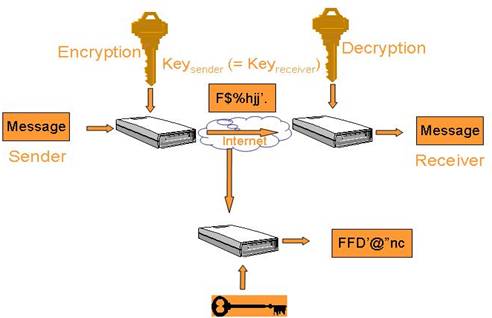
Seemingly pretty straight forward encryption where a key is used to encrypt
the message and the same key is used to decrypt the message.
In fact the processes of encryption and decryption are the same in
that a key is used to encrypt the plaintext and result is cyphertext.
Cyphertext is encrypted once again by the receiver using the same key
and result is effectively decryption and back to the plaintext.
In comparison
with asymmetric encryption or public key
encryption this is fast and efficient. Problem is the exchange of key between the parties
in a secure manner. The exchange of
key could happen personally through use of portable memory or as it is usually
done, through the use of asymmetric encryption.
The most frequently
used symmetric encryption algorithm is DES (Data Encryption
Standard). DES is the mathematical
procedure for encrypting and decrypting binary coded information and as such it
needs to be used in conjunction with ANSI (American
National Standard Institute)
Standards. With DES, key is a total of 64 bits, 56 bits of which are generated
randomly on the fly and used directly by the algorithm for encrypting and
decrypting. The remaining 8 bits are
used for error detection. DES encrypts
one 64-bit block at a time.
Triple DES
or 3DES is frequently used for very strong symmetric encryption. Three different keys are used to encrypt and
decrypt three times. Key1 is used to get
cyphertext1 from plaintext (in binary form).
Cyphertext1 is encrypted using key2 to get cyphertext2. Cyphertext2 is encrypted yet one more time
using key3 and result is cyphertext3. The decryption process happens in reverse
in that decryption starts with key3 and so on.
|
3DES
is compatible with DES. Why? |
|
|
Another
symmetric algorithm is AES (Advanced
Encryption Standard) that is mostly used by US federal bureaus. Blocks of 128 bits plaintext are encrypted
and decrypted using keys that can be 128, 192, or 256 bits long.
Other
algorithms that can be mentioned are Blowfish, Twofish, and Arcfour.
Note that
no encryption is 100% unbreakable and given enough time and computational power
through trial and error, encryption key can be worked out. Historically computational power has been
increasing and computers have become affordable and accessible (see Moore's law). What this means is that the strength of
128-bit symmetric key encryption (as an example) is very much relative to
affordable computational power that some adversary may have at his disposal and
that according to Moore's law, the strength of this encryption is diminishing
with time.
|
Think
of a short name and find ANSI binary code for each letter of the name. Then think of a binary key (could be 8
bits) and encrypt and then decrypt the name bi- by-bit using "Exclusive
OR" algorithm. Check that if you
encrypt one more time using the same key you are back to the name. |
|
|